In our previous Android security roundup we made a breakup of major Android versions for smartphones vs. their security. In this roundup we’ll be providing apps and system settings for better Android security.
If you are happy with your gadget and you don’t want a more recent Android device, there are some best practices to follow.
As we said, Nexus devices are the first to get the updates. It's good to know what to device to choose so the user will receive the quality and can be sure that information won't leak.
If your Android versions isn't fresh and you don't want to change your device, some other options are still available. Those can boost phone security and prevent data leak.
In many cases, stock Android contains a huge set of applications but they are mostly optional. Removing such applications won't break your system but can improve performance.
Advanced user's can even try to remove Google Play and replace it via F-Droid.
Also, be careful with root access. While it gives you a full system control, it can become a problem and threat.
Firefox for Android supports extensions which can be installed from the Firefox Add-ons website. There are fewer extensions for mobile Firefox as compared to the desktop one. uBlock Origin and AdBlock Plus are available and are recommended for privacy. Those can block malware websites, tracking activity, etc.
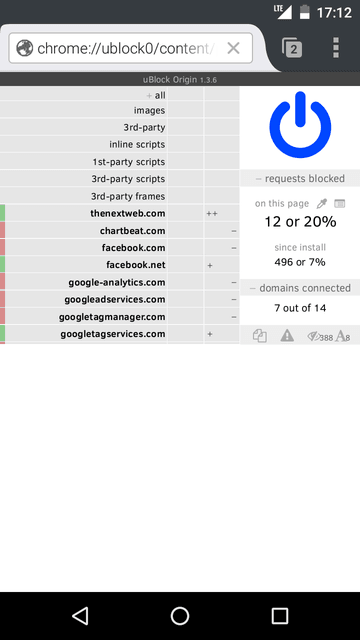
Beside add-ons, some browser options can be changed to improve security. It includes tracking activity, enabling Do-Not-Track option, disabling of sending Telemetry data and cleaning history information including cookies.
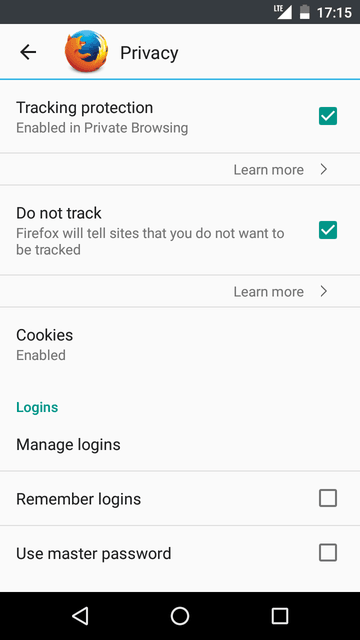
uBlock Origin is similar to its desktop analog and works without any issues.
Official website | Google Play
AdBlock Plus is a very popular extension, and it used to be available in Google Play. Some time later it was removed from there. Today the developers provide AdBlock Browser which is similar to the extension.
AdBlock Plus is still available for Android from the developers website, but it works only over Wi-Fi connections and requires some proxy configuration.
AdAway is another extension which blocks the ads and some other stuff. It modifies hosts file inside /system partition. It contains a list of ad serving domains, so that unwanted content doesn’t load.
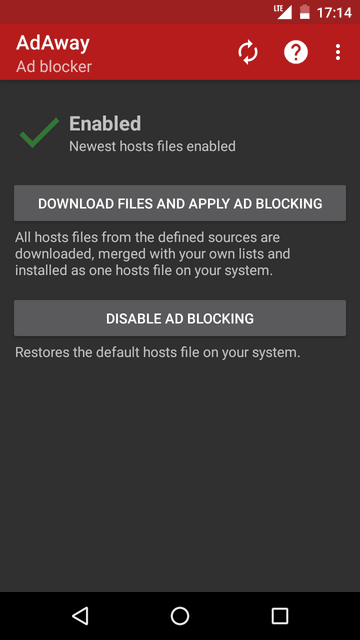
Some time ago this application was removed from Google Play because it not only blocks in-browser ads, but also ads inside applications. Nevertheless, this application can be installed from F-Droid catalog. It also requires device rooting because it modifies /system partition.
Offical page on GitHub | Google Play | FDroid page
AFWall+ is a firewall application. Android doesn't support blocking Internet access per application. With this application, it's easy to restrict access for certain types of network (i.e. Wi-Fi or mobile networks). It provides very flexible interface with checkboxes to block access for:
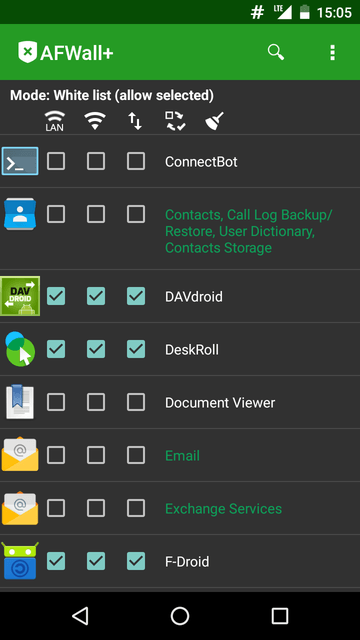
AFWall+ requires root access and won't work without it.
AFWall+ is a very good choice but only if you have root access. It’s not always a possibility, so let’s consider an app that works without it. NetGuard works mostly the same way as AFWall+ – restricts Internet access per application and per network type: Wi-Fi, mobile data.
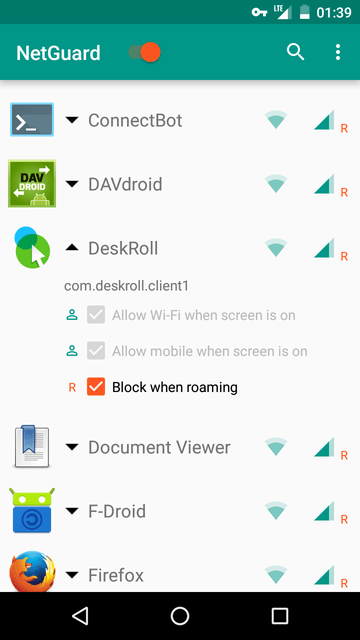
Google Permission control functionality was introduced in Android 6. It provides a graphical interface to restrict access to certain system parts. This is new behavior and not all applications can work smoothly. Sometimes, if applications support such behavior, Android will ask user whether to restrict access.
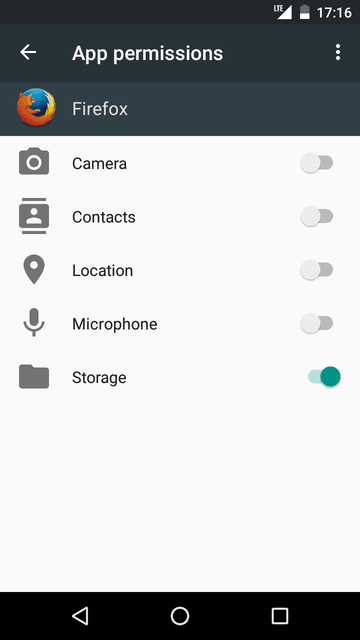
This behavior is very limited and doesn't indicate how it works. The whole process isn't transparent and allows control only for certain types of restriction (e.g., there is no Internet access control).
CyanogenMod introduced another version of Permission Control called Privacy Guard. It provides a more flexible way to control access for certain components of the system.
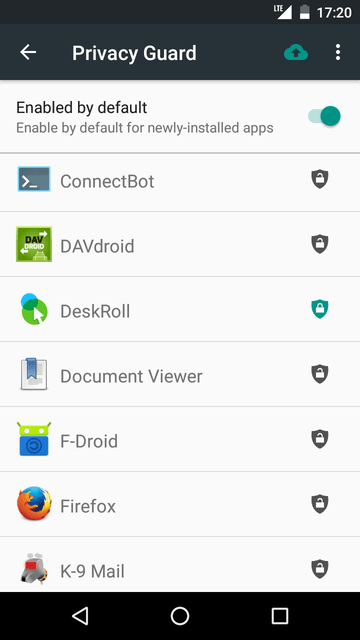
The earlier version was very limited. Current version indicates what action was made by application and when. It also possible to restrict access for such actions. The only drawback is that it’s available only in CyanogenMod.
Official project's page on Github | Google Play
XPrivacy is another way of controlling how applications access user information, phone settings and data. It built as an XPosed module (so it’s a requirement), also it requires root access. It provides access to low-level functions and allows configuring almost every aspect of Android system.
Advantages over stock Permissions Control and Privacy Guard:
1.Provides indications what features were accessed by applications (shows the exact function name and not only the group of functions).
2.Provides options for controlling different parts of Permissions.
3.Is available for stock Android versions starting with 4.0+.
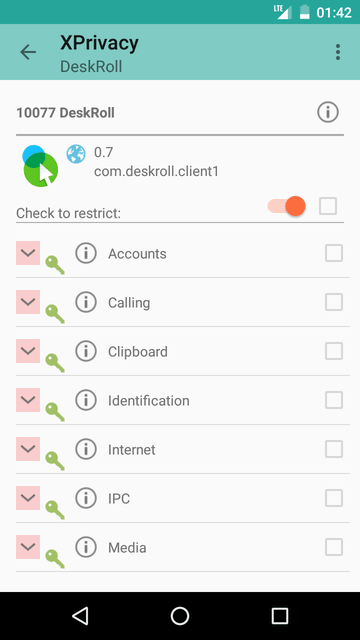
Application work as follows: for a certain requests it will return empty data to the application. For example, if the application requests access to the contact list, then XPrivacy will ask user (default behavior) and if user says No, then it will return an empty list. This approach is safe and in most cases it won't break anything, but it is wise to be sure what to restrict because some requests are very important (e.g., access to camera from a camera app).
This is an experimental application aimed to detect IMSI catchers aka fake mobile base stations. The idea of such devices is to intercept mobile user traffic.
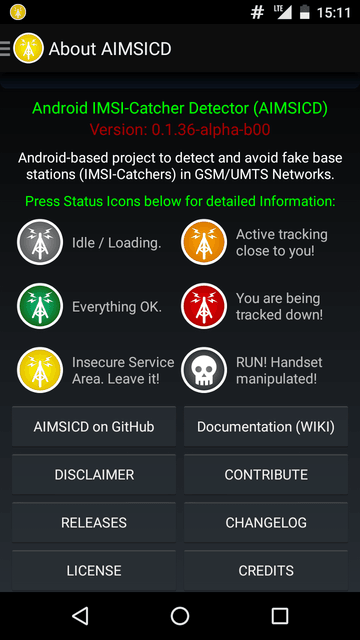
This application is mostly for enthusiasts. However, recent reports say that police forces are able to use such devices. Law abiding citizens are mostly not under surveillance, but in many cases such devices can be procured by criminals.
Tor Project official website, Android page
Tor is a secured anonymous network which aims to safeguard user privacy. It is available on many platforms including Android. It works like a proxy server locally on the users device. Tor enables the user to get a private IP and all traffic will then be invisible for the ISP and will be encrypted.
It is good to know that in some cases Tor is not the best choice. Sending private data through Tor is not a best practice. Tor points can as well be just regular users who are running some software on their own machines.
This is a different type of network for user anonymity. It's a different network type and it aims to make web browsing secure. I2P is entirely different from the Internet. It provides specific websites, with a different set of protocols and so on, and access to websites is provided via web browsers.
I2P websites look like http://domainname.i2p
These practices relate not only to Android, and they can be used pretty much on any device.